Questão número 635031
Consider the figure below.
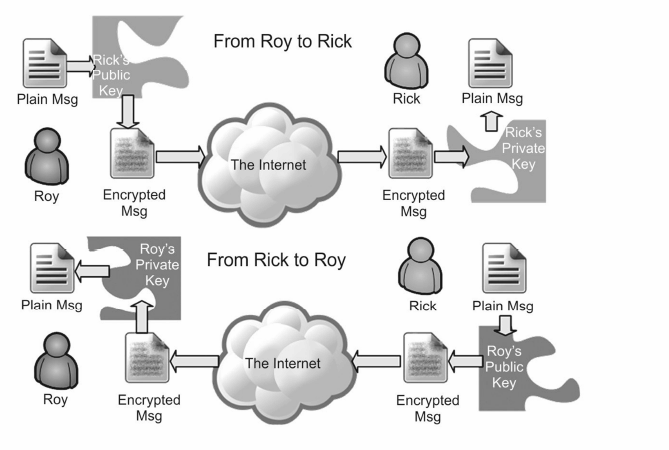
The correct way to describe the main concepts showing by the figure is:
- A. If someone wants to send a private message, he gets the secret key (directly from the receiver in an e-mail) and use it to encrypt the message. For a message back to the sender, the receiver grab his secret key and encrypt with that. So all the encrypting is done with the secret keys, and all the decrypting is done with the corresponding public keys.
- B. There's one major benefit to doing encryption this way: there is no need to send anything secret over an insecure channel. The public key goes out to the world, but it's not secret and it doesn't need to be. The private key can stay safe on a personal computer, where it was generated.
- C. The secret key cryptography method, also called asymmetric encryption, employs a secret key for both encryption and decryption. The sender uses the key to encrypt the plain message and sends the encrypted message to the receiver. The receiver applies the same key to decrypt the message and recover the plain message.
- D. Hash algorithms are typically used to provide a digital fingerprint of a plain message contents, often used to ensure that the message has been altered by an intruder or virus. Using public and secret keys, hash functions, then, provide a measure of the corruption of a message.
- E. The public key cryptography method, also called symmetric encryption, employs two keys that are mathematically related although knowledge of one key does not allow someone to easily determine the other key. One key is used to encrypt the plain message and the other key is used to decrypt the cipher text.


